
The Rise of Cloud Cost Management - Keeping cloud waste under control
Businesses migrate to the cloud for cost savings and scalability. However, poor cloud management can lead to cloud waste...

The pressure on businesses to prove compliance has never been higher. From SOC 2 to ISO 27001 to HIPAA, organizations must constantly show they meet strict security and privacy standards. Yet many teams still depend on outdated, manual methods — endless spreadsheets, screenshots, and checklists. The result is wasted time, avoidable errors, and unnecessary stress when audit season arrives.
The solution? Automation. By shifting from manual processes to automated compliance, businesses can save time, reduce costs, and maintain a stronger security posture. Let’s break down why the old way is failing — and how automation platforms like iCompaas change the game.
Manual compliance is slow, repetitive, and vulnerable to human error. Teams spend countless hours collecting evidence, updating policies, and mapping controls — all while juggling core business priorities. The bigger the environment, the worse the problem becomes. Even the most disciplined teams struggle to keep evidence current, which often leads to gaps that surface only during the audit itself.
In other words, manual compliance isn’t just inefficient — it’s risky. It distracts teams from real security improvements and leaves organizations exposed to mistakes that can derail certification efforts.
Relying on outdated compliance processes introduces very real risks.
Audit failures can damage your reputation and cost valuable business opportunities.
Security gaps may remain hidden until exploited by an attacker.
Excessive costs pile up as IT and security teams sink hours into work that could be automated.
For startups and growth-stage businesses especially, one failed audit could mean losing investor confidence or missing out on enterprise deals. Manual compliance isn’t just a burden — it’s a barrier to growth.
Compliance automation flips the traditional model. Instead of chasing evidence once a year, you build compliance into your daily workflows. With iCompaas, organizations can:
Automate evidence collection — policies, configurations, and logs are pulled directly from your systems, no screenshots required.
Monitor compliance in real time — issues are detected and flagged before auditors ever see them.
Stay audit-ready all year round — reducing audit prep from months of chaos to just a few days of review.
Standardize controls across environments — ensuring consistent enforcement whether you’re on AWS, Azure, or GCP.
This proactive approach not only saves time but also strengthens overall security by catching problems early.
iCompaas was built for businesses that need to be secure, compliant, and cost-efficient without hiring an army of compliance staff. The platform brings together:
Cloud Security Posture Management (CSPM) to identify and fix misconfigurations.
Automated policy enforcement that reduces human error and keeps controls consistent.
Audit readiness tools for frameworks like SOC 2, ISO 27001, HIPAA, GDPR, and more.
Cost optimization insights so businesses don’t just stay compliant — they also avoid overspending on cloud resources.
With iCompaas, compliance is no longer a bottleneck. It becomes a competitive advantage.
Manual compliance wastes time, increases risk, and drains resources.
Automation transforms compliance into a continuous, proactive process.
iCompaas helps businesses save time, reduce costs, and achieve certifications with confidence.
Don’t let manual compliance hold your business back. 👉 Book a demo with iCompaas today and see how automation can save your team time, money, and stress — while keeping you secure and always audit-ready.
Explore more insights and strategies from our security experts

Businesses migrate to the cloud for cost savings and scalability. However, poor cloud management can lead to cloud waste...
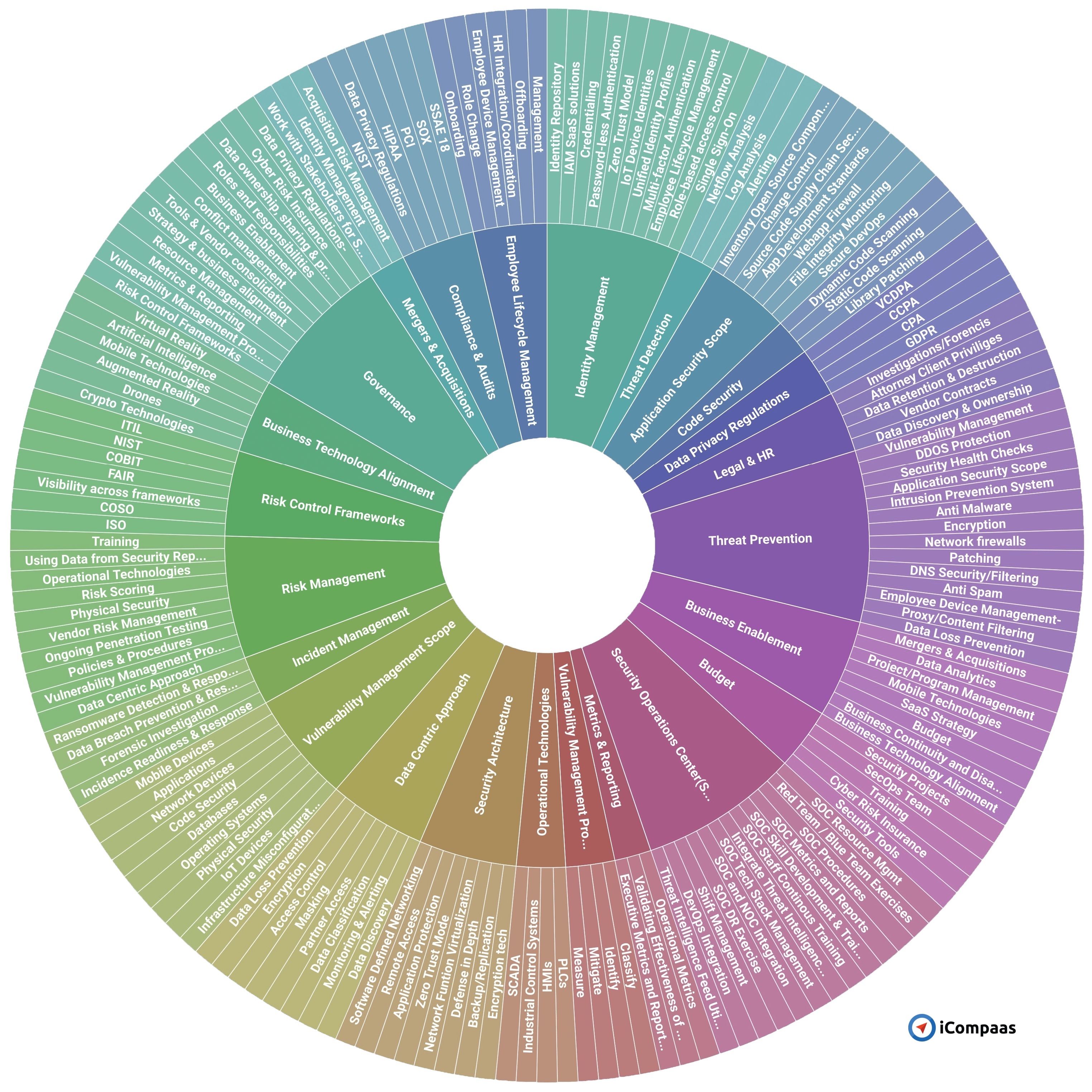
Looking at the simplified two level taxonomy of the cyber security topics is key for building understanding of the topic...
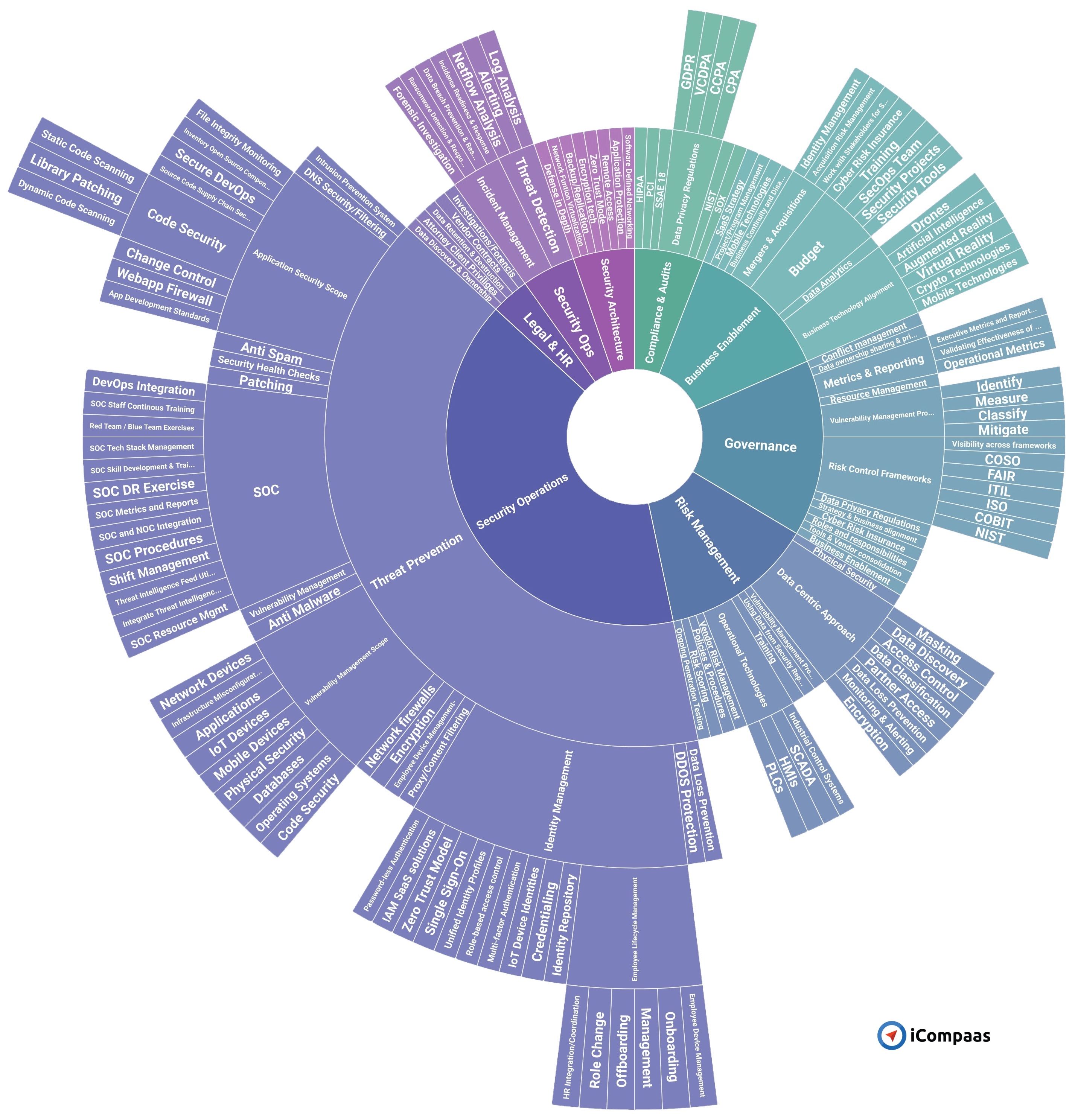
Looking at Multi level taxonomy of the cyber security topics though daunting is educational and very necessary.